Integrated Windows authentication
You can easily implement single sign-on for GAPTEQ applications in the internal network (intranet) with integrated Windows authentication for AD users and increase user convenience.
In this article you will read the following content:
Activate Windows authentication in the IIS web server
Activate Windows authentication in GAPTEQ
Activate Windows authentication in Firefox
Your requirements for implementing integrated Windows authentication:
- Configure the GAPTEQ server for operation with an Active Directory user (Microsoft Active Directory feature tip)
- Operation in the internal network with the Microsoft Active Directory (AD)
- Login only possible for Active Directory users (please note: local GAPTEQ users can no longer log in in this configuration)
- AD user requires read rights for the GAPTEQ-Web directory
Note! While Internet Explorer, Edge, Chrome and Opera automatically support Integrated Windows Authentication by default, the functionality must first be activated for Firefox.
Tip! Logging in to the repository in the GAPTEQ Designer is not affected by the use of Integrated Windows Authentication and continues to work with direct entry of username and password.
GAPTEQ Web file rights
After installing GAPTEQ Web, AD users must have read access to this folder (C:\Program Files (x86)\GAPTEQ\GAPTEQ Web).
After installation and after an upgrade, please authorize your AD users for read access to the GAPTEQ Web folder and the files it contains.
1. Activate Windows authentication in the IIS web server
- In the IIS Manager, select “Sites” > “Default Web Site” > “GAPTEQForms” in the “Authentication” area.
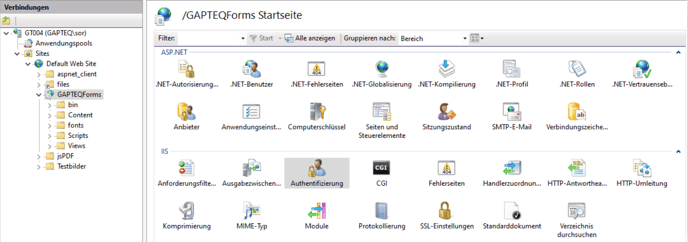
- “Anonymous authentication” must remain activated in order to deliver public pages that do not require a login.
- “Windows authentication” is activated.
- All other methods must be deactivated.

2. Activate Windows authentication in GAPTEQ
- Open the appSettings file with text editor for editing:
C:\Program Files (x86)\GAPTEQ\GAPTEQ Web\appSettings.json - Set the value for IntegratedSecurity to “true”

If you want to enable login for internal GAPTEQ users at the same time, also set the value for Internal to true. A login dialog is displayed in this configuration. Internal users can log in and AD users can log in directly with a click of a button without a username and password.
3. Activate Windows authentication in Firefox
Note! A blanket activation for SSO is not provided in Firefox. All hosts that are to be allowed for SSO must be specified individually. This can be done in the browser configuration or via group policies.
For a configuration via group policy, please contact your system administrator.
- Enter the following command in the address bar of the Firefox browser:
about:config
After confirming the risk warning, the configuration page opens.
- Search for
and select in the hit list:
network.automatic-ntlm-auth.trusted-uris
- The host names are entered in the input field. Multiple hosts are separated by commas.
![GAPTEQ Logo links weiss.png]](https://knowledgebase.gapteq.com/hs-fs/hubfs/GAPTEQ%20Logo%20links%20weiss.png?width=223&height=54&name=GAPTEQ%20Logo%20links%20weiss.png)